Social Practice Theory and Cyber Security
Social Practice Theory and Cyber Security
Let’s start with some housekeeping. If you came here looking for methods or answers you can apply tomorrow, I’m afraid you’ll be disappointed. I’m just very curious and this is something I’m currently exploring.
In the last 6 months, I was introduced to Social Practice Theory by Marc Burgauer and Chris McDermott in their workshop on ‘Maturity Mapping” and I’ve been doing some reading on it having just finished a great book by Elizabeth Shove titled ‘The Dynamics of Social Practice: Everyday life and how it changes” and I’m feeling the need to organise my thoughts on what I’ve learned and how I think Cyber Security can benefit from looking at what we do through the Lens or Frame of Social Practice, so what better way than to write a blog ?
So, first to define Social Practice Theory, I’ll be leaning on Wikipedia:
Social Practice theory is a framework for social science researchers to describe how individuals in different societies around the world shape and are shaped by the cultural atmosphere in which they live. It attempts to articulate the ways in which identity and individual agency rely on and produce cultural forms.
These principles are usually written and applied at the societal level, but can also be applied to organisational practices (Maturity Mapping is a brilliant application of that). For all of the practices we have in organisations (think designing, operating, socialising, etc) we can think of our role as people as the practitioners of such practices and each of those practices are made of different types of elements.
By elements we mean: materials — including things, technologies, tangible physical entities, and the stuff of which objects are made; competences — which encompasses skill, know-how and technique; and meanings — in which we include symbolic meanings, ideas and aspirations. We go on to argue that practices emerge, persist, shift and disappear when connections between elements of these three types are made, sustained or broken.
Shove, Elizabeth. The Dynamics of Social Practice (p. 14). SAGE Publications. Kindle Edition.
I have a particular interest and wish to explore (I’d most welcome contributions and commentary) security practices in organisations, in particular Threat Modelling and Risk Analysis.
practices are defined by interdependent relations between materials, competences and meanings.
What the book creates a case for is that “material, meaning and competence are not just interdependent, they are also mutually shaping”. I think this is huge, as we seldom think of the materials or tools we use as shaping both the competences and actual meaning of practices we perform. Let’s use 2 examples, related to Threat Modelling and how one might consider growing maturity in each of those practices.
Exploring Threat Modelling through the Lens of Social Practice
Note: the content of the maps (apart from the maturity parts) is close to verbatim based on Adam Shostack’s book on Threat modelling, which I still think is the Bible equivalent for Threat Modelling. Also, I’m less interested if use of CWE is actually more or less mature than CAPEC for instance , but happy to have that conversation too.
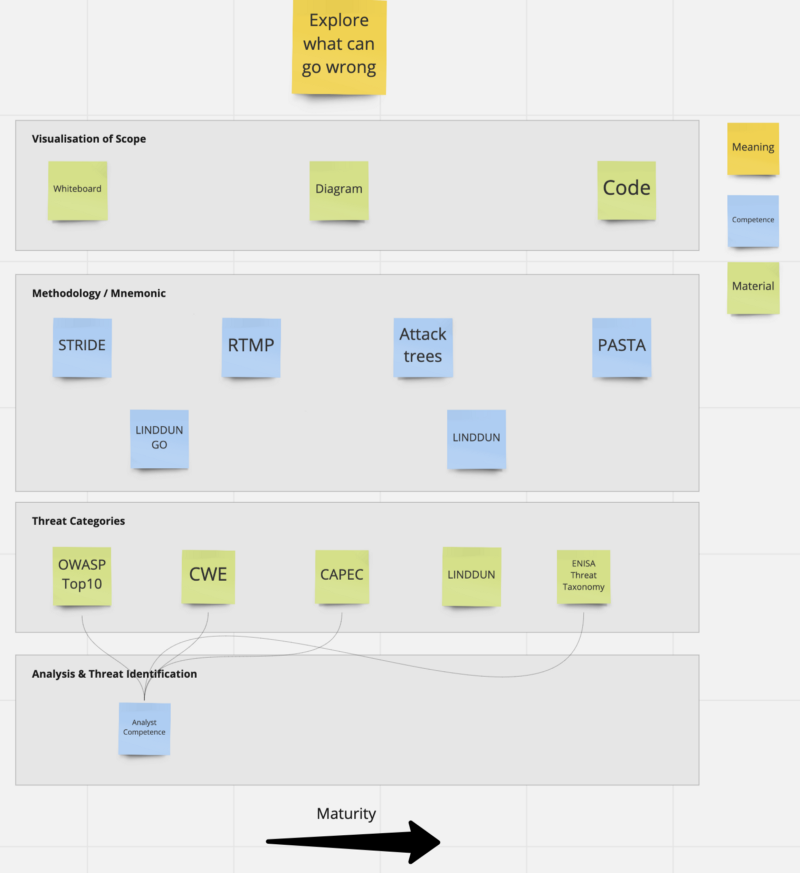
Different parts of asking ‘what can go wrong’ can be broken down into different competences from practitioners (or required competences) and materials which support them. Starting at the top in terms of visualising the scope of what we’re Threat Modelling. If you’re just introducing the practice of Threat Modelling, you’d probably do well to start on Whiteboards and that coupled with an understanding of the STRIDE mnemonic and OWASP Top 10 is likely to be more than enough to get you started. But as you wish to scale your programme, all of those might be holding your progress and finding ways to commonly visualise (re-use existing diagrams to keep references) the Threat Model becomes important and if you’re running hundreds of services, probably having your Threat Models as Code becomes a scaling requirement at the risk of being a constraint to your overall development process.
In a similar vein, just thinking in terms of the STRIDE mnemonic will definitely get you going but if you wish to have repeatability of the process without the more experienced practitioners in the room, adopting a methodology becomes important and even past that if you wish to connect the outcome of the practice with something else (like PASTA allows to have a Risk-driven threat enumeration approach) even more, as the outcomes then become something part of the management system which will be audited yearly so you want to have some assurance of its quality as well as think of threats more widely, and not just an OWASP Top 10.
Now using an example of “how good a job have we done?” and in particular ‘Test Checking’ as the last question of Threat modelling as per-Adam.
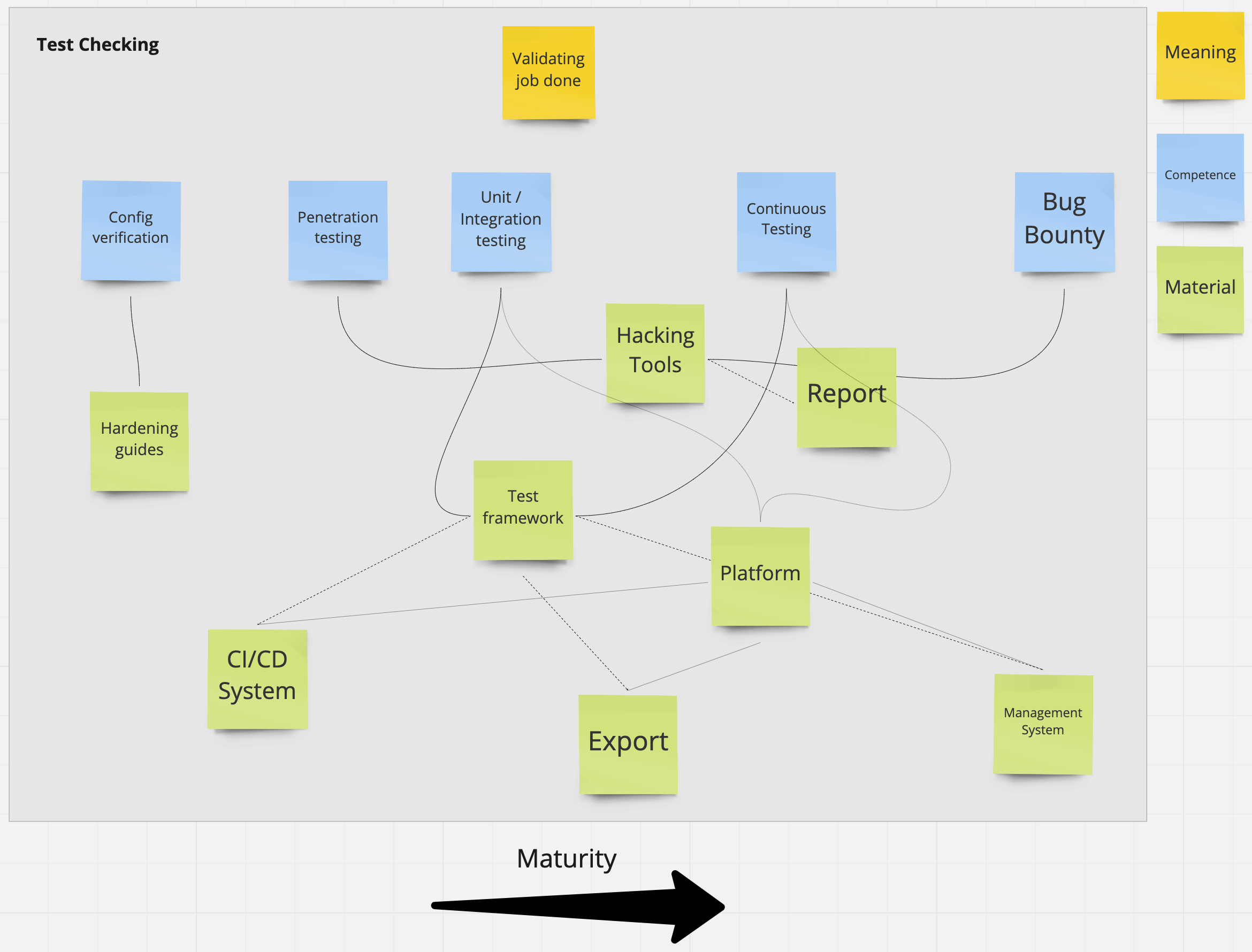
For this one, validating the job done can start as simply as eye-checking that a particular hardening has been applied which can be be done manually with vendor hardening guidelines as the material (for some threats), or include a combination of unit and integration tests which validate that the controls are being applied successfully.
Penetration tests are the ‘old-world’ Assurance Rolls-Royce (if it passes the pen-test, we’re good) though in 2020 we should all know better by now, which we need some hacking tools and a report to come out of it as the materials used in such activity.
Testing, whether individually or continuous, as a competence will require a test framework or at least a platform to run tests on (particularly thinking about Docker, since it’s one of my preferred ways to run automated tests in CI/CD). But when thinking about the results we get from running them, we can and usually start by storing the output as artefact in CI/CD system itself, something slightly more maturer would be to export those results somewhere that other stakeholders (those who can only read Excel, Word or PDFs :)) can participate in the practice as well but eventually you’d like to be in a place where exceptions are managed in code and that outputs generate artefacts (read tickets) in a management system for follow-up in an automated fashion.
Finally, if you’re not already doing all these things (ie you have a social practice of Threat modelling in place that is delivering on these) I’d argue you shouldn’t even consider being part of a Bug Bounty programme, as experience tells me you’re likely to find yourself fighting hard uphill battles internally in your organisation where many things identified by the Bounty hunters has the potential to become a PR issue, so a lot has to happen for you to be in the position to adopt that safely.
Social Practice as a lens to troubleshoot your security processes
Where I think Social Practice Theory is most helpful, is in helping frame and consider the linkages between the different elements of the security practices in our organisations. This should allow us to ask powerful questions on how to iterate and improve them. Some examples of what I believe are powerful questions would be:
- Does everyone who need them have the competences to perform this security practice ?
- Considering the materials I use to manage the output of the practice, are they driving certain types of behaviours or inhibiting others ? (a great example is how Risk Registers and Risk matrices almost force you down the road of of only dealing with tail risks, when realistically those are the ones where you have the least chance to actually create appropriate controls for)
- Do I actually need a new security practice, or are there existing practices which could be leveraged by changing existing materials to achieve the same security benefit ? (this is particularly important in a DevOps world)
- Does everyone performing a practice share a common meaning to why it is important ? and if not, could that explain its performance ?
- Does it make sense to have a big formal, multi-tiered Threat modelling process if your Engineers don’t currently know what STRIDE is ? or put in a different way, what’s the point of adopting off-the-shelf materials if you don’t currently have the competence to take advantage of them and your teams are likely to feel overwhelmed by it ?
Duguid goes on to suggest that the necessary knowing how (i.e. knowing how to decode) is unevenly distributed because it is itself an outcome of prior experience. This suggests know-how can only travel — by means of abstraction and reversal — to sites in which practitioners are already prepared to receive it because of prior, first-hand, practice-based experience.
- Are your security practices framed as “something they do for the Security team” or do the teams see it as an inherent part of their jobs ? and if not, how can we think of the necessary competences and materials which can help make that transition ? or put in a different way, is security part of your approach to building quality products and is it managed as such ?
The extension of one set of meanings sometimes implies the contraction of others.
There are many more powerful questions which can help guide our transformation objectives to support us in integrating practices which will provide better assurances of building secure products.
Social Practice as lens to tailor practices to our context
Another common mistake I’ve seen across many organisations relates to the adoption of practices and frameworks which are (or not) accepted as industry-standards or that are at least specified in a way which can be “copy-pasted” into your environment.
While it’s good that we have sound basis to start from, and from a Governance and Compliance perspective, it helps that we can position our approaches in a way which self-explains adequacy and due diligence (if you’re audited, it’s easier to explain to a non-techie auditor that you use a CIS benchmark than it is to walk him through the tech details of how you decided to harden your systems, for instance).
Social Practice reminds us that we need to understand how to localise the practices to the context we’re applying them to.
This suggests know-how can only travel — by means of abstraction and reversal — to sites in which practitioners are already prepared to receive it because of prior, first-hand, practice-based experience.
This is one of the reasons why I like to spend a few months Threat modelling just using STRIDE or LINDDUN GO to establish a shared vocabulary, before introducing more methodical methodologies.
elements of know-how are typically modified, reconfigured and adapted as they move from one situation or person to another and as they circulate between practices.
acquiring new forms of skill often takes time. By contrast, meanings (i.e. forms of association) can change and emerge and can travel far and fast. That said, the effective appropriation of meanings and competences depends on local capacities to embed, ‘reverse’ and interpret. Such capacities are unevenly distributed and are, in turn, born of practices past.
Being open NOT to adopt practices “by the book” but being vigilant at the best ways that work in your context and produce the right outcomes is of key importance. Once your constituency acquires the necessary Competences to perform them, let them adapt them all they want. That’s what people do. Being too rigid on implementation details, is likely to have a negative effect and change the meaning of the practice to those around you.
This is also a big reason why I prefer NOT to create security practices, but instead assess Engineering practices and see how we can leverage them to achieve the security objectives. For instance, not creating a workflow to manage vulnerabilities per-se, but associate vulnerabilities with ‘Bugs’, ‘Improvements’ or whatever issue types you use and frame the management of security in those terms.
Conclusion
The conclusion is that I don’t have a conclusion 🙂 This is a topic that is really resonating and that I wish to explore a bit more, particularly to explore intersections between Risk Management and Threat Modelling processes.
The key insight, which I also believe is very relevant to approaches to Security Awareness, is that we in Cyber Security have been focused too much on the ‘individuals’ and targeting individuals as part of our efforts to make your organisations more secure but, through the lens of Social Practice, we now have the opportunity to assess the linkages between individuals and practices (practices as performances as practices as entities) as another tool in our arsenal to create better outcomes for our employers.
Reference: Shove, Elizabeth. The Dynamics of Social Practice . SAGE Publications. Kindle Edition.