Security for the 2020s: The Skills and Talent problem
Security for the 2020s: The Skills and Talent problem
If you’ve been following security news and any prominent security speakers for the past year or two, you’ll certainly have come across 2 differing views regarding skills and shortage.
On one hand, there’s the media and corporate message that we have a serious skills and talent shortage as corporates can’t seem to hire security people and keep losing them, and on the other hand we see newcomers into the industry and prominent security speakers speak about how we’re trying to hire all wrong and not creating enough entry level positions, and the ones we do have we create unrealistic requirements for entry such as certifications and years of experience. I’m more of the latter group-type.
In this post, I’ll explore a few different aspects of this. First, we’ll talk about Skills and Talent and what you can do about managing that constraint (this section will be more geared towards security managers or HR pros hiring security expertise). Next we’ll look into what skills are being required of us (security pros) now, and what came before and the market is still flooded with skills which have now become commodities that aren’t enabling strategic advantage to our organisations anymore, and finally a future looking view of skills which are emerging and seem to be the required by the most advanced organisations and are likely to be job requirements at large in the next decade.
I’ll then end with a list of resources you can use to explore all of the above.
We do not have a shortage of skills or talent, but there are economic issues at play
Let’s start with economics. A well known economic pattern (meaning it’s business as usual and has been business as usual for millennia) is that of “Creative Destruction”. This is directly related to innovation and it asserts that its effect is “to devalue, if not destroy, past investments and labour skills” and also that it is “embedded in the circulation of capital itself”.
The paradigm shifts which are still on-going of DevOps and has already started happening with Serverless, require fundamentally different approaches to Security and securing the produced assets which most of the industry is still struggling with, not realising that the skills they brought to the table to secure the “old world” are devalued and soon to be destroyed as the effect of “Red Queen” forces organisations of all industries and sizes to adopt practices which enable business agility and adaptability at scale (what DevOps is about).
This seemingly unrelated primer serves to position my hypothesis that we don’t necessarily have shortage of skills or talent, we mostly have security organisations who don’t fully understand the problem they’re trying to solve and are bringing “knives to a gun fight” and that reflects on the job adverts they write, the people they try to hire and perpetuates the appearance of a shortage of available skills. The old adage “it takes one, to know one” would apply here.
I particularly like Andrew Clay Shafer talks on talent and skills shortage which I’ll quote a lot here, and particularly his definitions for skills and talent:
Skills are the ability to use one’s knowledge effectively and readily in execution or performance
Talent is a special ability that allows someone to do something well
So connecting the 2 parts together, I’’ suggest the following:
There is no skills shortage — most have a poor understanding of what they actually need to be successful or the skills which need to be leveraged to improve their security posture
Examples: you’ll probably have a problem communicating security. You probably need someone with a marketing background and a security interest. you’ll probably have a problem with automated security testing: you probably need a QA engineer or Developer with a security interest.
I’ll say it loudly for those in the back: THE PROBLEMS YOU REALLY NEED TO SOLVE, ARE UNLIKELY TO BE SOLVED BY SOMEONE HAVING A CISSP OR A CISM (maybe they are, if you’re lucky. but that’s a bad way to frame the conversation and a great way to be complaining for another 5 years that you can’t find talent to solve your problems).
Figure out what you need, and skills which can be leveraged to deliver and improve on it. Creative Destruction means that there isn’t a whole lot of supply of people ticking all the boxes, so you need to be strategic and targeted about this. Give good people a chance.
There is no talent shortage — you probably don’t have a mission worth getting out of bed for or a culture which fosters continuous learning and growth where people feel psychologically safe. I won’t go into more details for the sake of not ranting, but please check Andrew Clay Shafer reference talks at the bottom for more info on this.
But you will need to figure out how to be a learning organisation, and that means setting up new people to succeed and “becoming graduate studies of the skills you need to succeed” as Andrew Clay Shafer says. You won’t get that externally, because that’s highly dependent on your culture.
Skills the industry seems to require from Security teams
Those following me for longer, know I’m a big fan of Wardley Mapping (which you can learn more about from LearnWardleyMapping.com) so I have a map to discuss this session. This one is based on information by Michael Brunton-Spall and Sounil Yu and some research I’ve done through analysing CVs.
For those unfamiliar, with #WardleyMapping you can think of the Purple elements as commoditised skills (market is flooded with them and they’re not differentiators though a lot of legacy businesses are still looking for them), the ones in Blue represent skills which are currently high value and the market is asking for (though I believe it’s reaching or reached its peak and will soon start declining in strategic value for the individual as differentiator) and in Amber are the skills which aren’t yet as requested by industry but there are signals that they’re the next frontier for the security professional for the end of the next decade). All skills have a cycle that from left to right, so this is continually changing and what today is a strategic differentiator for the individual will become next decade’s commoditised skill as new ones emerge.
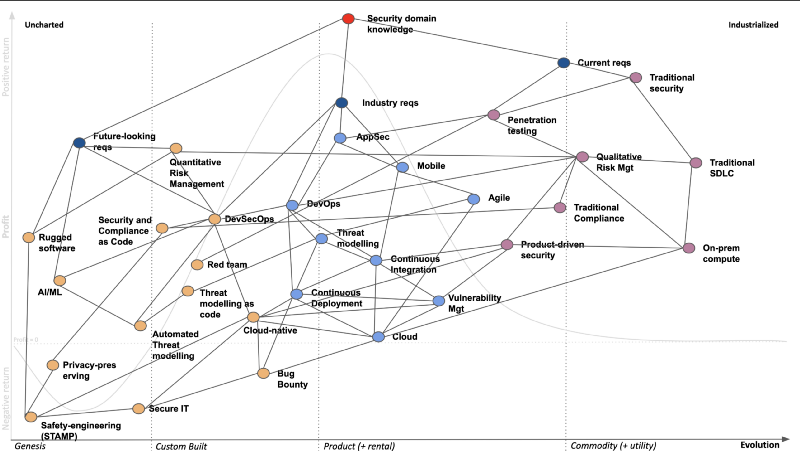
All maps are imperfect representations of landscapes, so I’m happy to get feedback on the maps and improve on them. I won’t go into detailing all of them but in the section below, you’ll find some resources on a good portion of them and feel free to reach out to me to ask for any further guidance.
Resources to acquire some of these skills
For acquiring skills relating to current Industry needs, I would propose the following:
- Focus on Appsec
There are tons of good resources on AppSec these days. I’m a particular fan of OWASP. 2 good resources to start with would be:
https://www.owasp.org/index.php/Category:OWASP_Application_Security_Verification_Standard_Project
https://www.owasp.org/index.php/Category:OWASP_Top_Ten_Project
- Learn to Threat Model
The authoritative book on Threat Modelling is still Adam Shostack “Threat Modelling: Designing for Security” which you can get from Amazon here
- Understand Agile and DevOps
This is relevant for both current security professionals which are getting their skills superseded and for any people wishing to pivot to Infosec.
Three books I’d highly recommend (and in this order) would be:
“The Phoenix Project” by Gene Kim et al. This novel is particularly good at portraying the struggle of the CISO in adopting DevOps from an “old world skills” perspective.
“The DevOps handbook” by Gene Kim et al
“The Unicorn Project” by Gene Kim et al
- Understand DevOps tools
A CI/CD platform like Jenkins or Gitlab, Docker, Kubernetes, Ansible, Terraform. Know what those are and the basics of them.
- Understand and play with security tools for CI/CD integration
Create your own lab, and experiment with running open source security tools on your lab pipelines. DevSecOps Studio project is a great way to start, and it’s all open source. You can learn things about how to check for insecure code, for insecure dependencies used in software, how to do dynamic vulnerability scans etc.
- Get a DevSecOps certification
FULL DISCLOSURE: I’ve recently taken a role with Hysn Technologies (who own the Practical DevSecOps brand) as Strategy Director, but I was already a massive fan of them and have been advocating for their courses for about 2 years now. The course is brilliant (I took it in 2018) and I would highly recommend due to its practical nature. You can find all about it here
For acquiring skills relating to future Industry needs, I would propose the following:
- Everything as Code is almost here. Learn to Code
You should learn to code something. Python seems to be a good choice and is also relevant for the Serverless world, but anything would do really.
- Explore Cloud Native Foundation solutions
Learn about Cloud Native projects here: https://www.cncf.io/projects/ get hands-on or at least functional understanding of the most important ones as you’re likely to find many organisations increasingly using them. Some particular ones to mention are Kubernetes, Prometheus, OpenTracing, OpenTelemetry and some which are specifically security focused would be Open Policy Agent, In-toto and Falco. Grafeas.io is also worth your time though not CNCF. but Open source by Google.
- Data Science, AI and Machine Learning
Unfortunately I can’t remember the author, but I remember reading somewhere about a year ago that those who can teach AI and develop good models will be the equivalent to overlords of the future world. That sounds cool, so you should probably learn some of that 🙂 This also includes Data Science which is likely to be a good first step
- Safety and Resilience Engineering
Safety and Resilience engineering, I covered in this post on addressing the Engineering problem so would recommend you read that
- Observability
I myself want to do much more learning about this in 2020, but I believe there’s a lot of untapped potential in exploring Observability solutions like honeycomb.io, OpenTelemetry for security purposes.
Conclusion
Hopefully this was informative to both current and future security professionals on how we can get better prepared to the skills we need to be successful in the next decade. This is by no means an extensive list and I reckon the industry is going to continue shaping as it has thus far, but what I’m almost certain of is that resilience and appreciation of security practices and team topologies will be evolving and we’ll do well in learning from others who have integrated security as part of their overall quality assurance and not “something those guys over there do” as the latter is not scalable to the demands of the marketplace going into the next decade