Security Strategy and the ‘Why of Purpose’
Security Strategy and the ‘Why of Purpose’
I’m a big fan of Wardley mapping, which includes a lot of elements which are influenced by Chinese strategic thinking into a framework that is easy to understand for us, Westerners. I’ll be doing some blog posts on how I think Security Strategy can be developed using Wardley mapping principles
For those less familiar, this is what the Strategy Cycle from Simon Wardley looks like:
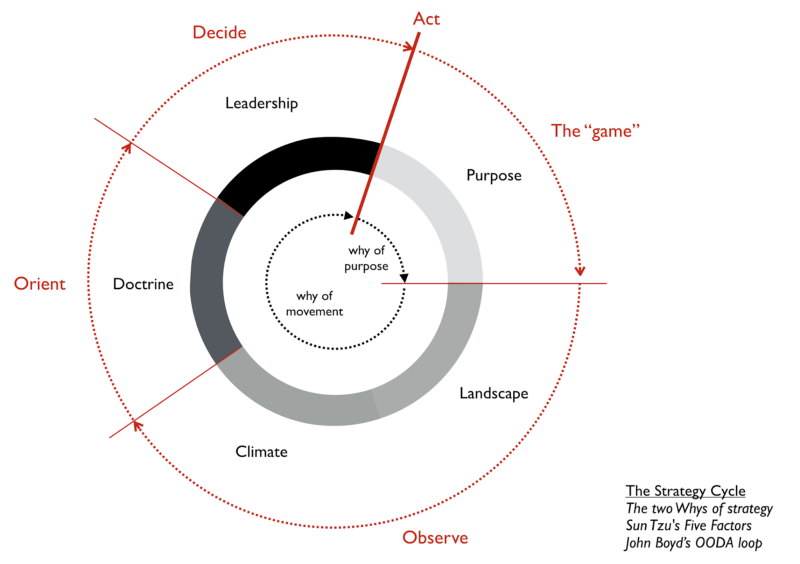
In Wardley mapping, there are 2 types of Why. The Why of Purpose and the Why of movement.
Benjamin Mosior from LearnWardleyMapping.com defines Purpose as:
In Wardley Mapping, Purpose is “the game” being played. It defines the scope of what you are doing and why you are doing it. It may be a moral imperative or just what motivates you to come to work every day.
Purpose is the first step in the strategy cycle. Because many leaders do not understand the importance of Landscape, Climate, and Doctrine, they commonly shortcut the cycle and jump straight from Purpose to strategic decisions in Leadership. This “strategy by gut feel” is an inadequate approach for strategic thought.
This is where so many organisations start from a non-optimal place, and I’m convinced it has lot to do with personal biases from Security leaders (as does everything else probably) and the resulting Gut Feels for what they believe is required to tackle the challenges they face.
The Risk Management CISO, The Engineer CISO, The Developer CISO or the Business CISO will tend to frame their strategy in the terms most familiar to them, and as we know security requires a multitude of aptitudes and attitudes so overly focusing on one is likely to alienate a good part of the team responsible for its delivery.
Security Visions and Mission statements and why you should probably bin them
swardley created a long time ago a Strategy Generator as parody to the work most/many consultants do, whether they’ll admit it or not, and how right it is and how many actual consultants told him that it was useful is both alarming and appalling. This is what a secure strategy could look like in the auto-generator

Let me start out by saying that as a Security professional with a long career in different types of roles and organisations, I’m yet to see a single Vision or Mission Statement from a Security Leader or CISO that, understanding the local landscape, didn’t immediately make my eyes roll to the back of my head and stay there for a few minutes. Maybe I’m just cynical.
To me, that’s akin to what swardley refers to as the “tyranny of action”, in that it’s also about act, invest, deploy and repeat with little to no effort on fully understanding Landscape, Climate and applying Doctrine.
Benjamin Mosior created a great visualisation for this.
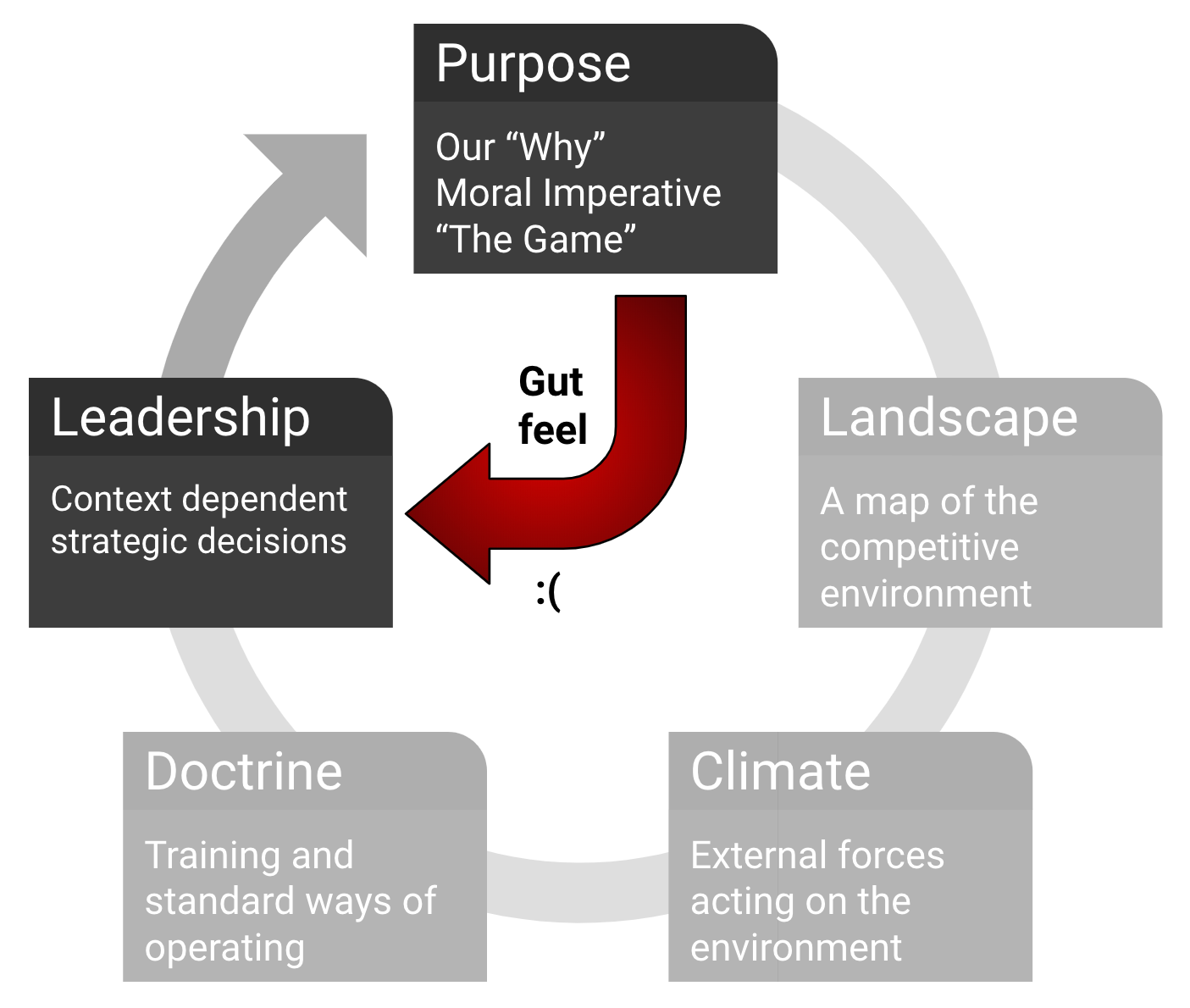
Experience tells me that for all organisations I worked in, my security colleagues shared a lot of the “eye ball rolling syndrome” I also got in the yearly kick-off’s of our security programmes so I know I’m not alone in this.
They usually paint a picture so bright and/or abstract of what “could one day be”, that it fails to motivate the team on what they can do to help achieve it. And if the people who will drive it don’t believe in it, you don’t stand a chance of getting there.
The Tyranny of Control
Phil Huggins recently mentioned his general dislike for controls, to which I largely agree with as well. We were discussing more at an operational level, but I believe this has implications at the strategic and grand-strategic levels too.
I believe a big part of the problem, is that our accepted security regulations, standards and practices are overly focused on Security as controls which are put in place to either prevent or reduce likelihood of bad things happening, and that’s so embedded in everything we read and do as security professionals that it becomes hard to acknowledge, let alone do something about it.
This means that when going from Purpose to Leadership through Gut feel, a lot of our security programmes will be spent deploying and improving controls. Now, I don’t think controls in and of themselves are a bad thing, we are hired and exist as a discipline to reduce the impact of likelihood of bad stuff which controls generally help mitigate.
What I am arguing is that a vision overly focused on Controls will have a narrow scope for driving actions as it will engage and orient only to the extent that someone (both security teams and organisations we work for) are concerned about a particular bad outcome. It’s a loser’s game as it puts us in the position to keep arguing why something could be really bad as justification for our security spend.
This is the strategy equivalent of a ‘Signature-based AV’ that is no longer a good practice in security for almost a decade now. It puts in a position to constantly find, enumerate and find signatures to deal with “known-badness” and it’s game that makes it impossible to be on the front foot and not in a reactive mode constantly.
Moving from Control to Enablement

In the “Map of Security mapping”, I argued that security should be a business enabler and not just something we do for compliance sakes, but most aren’t there yet.
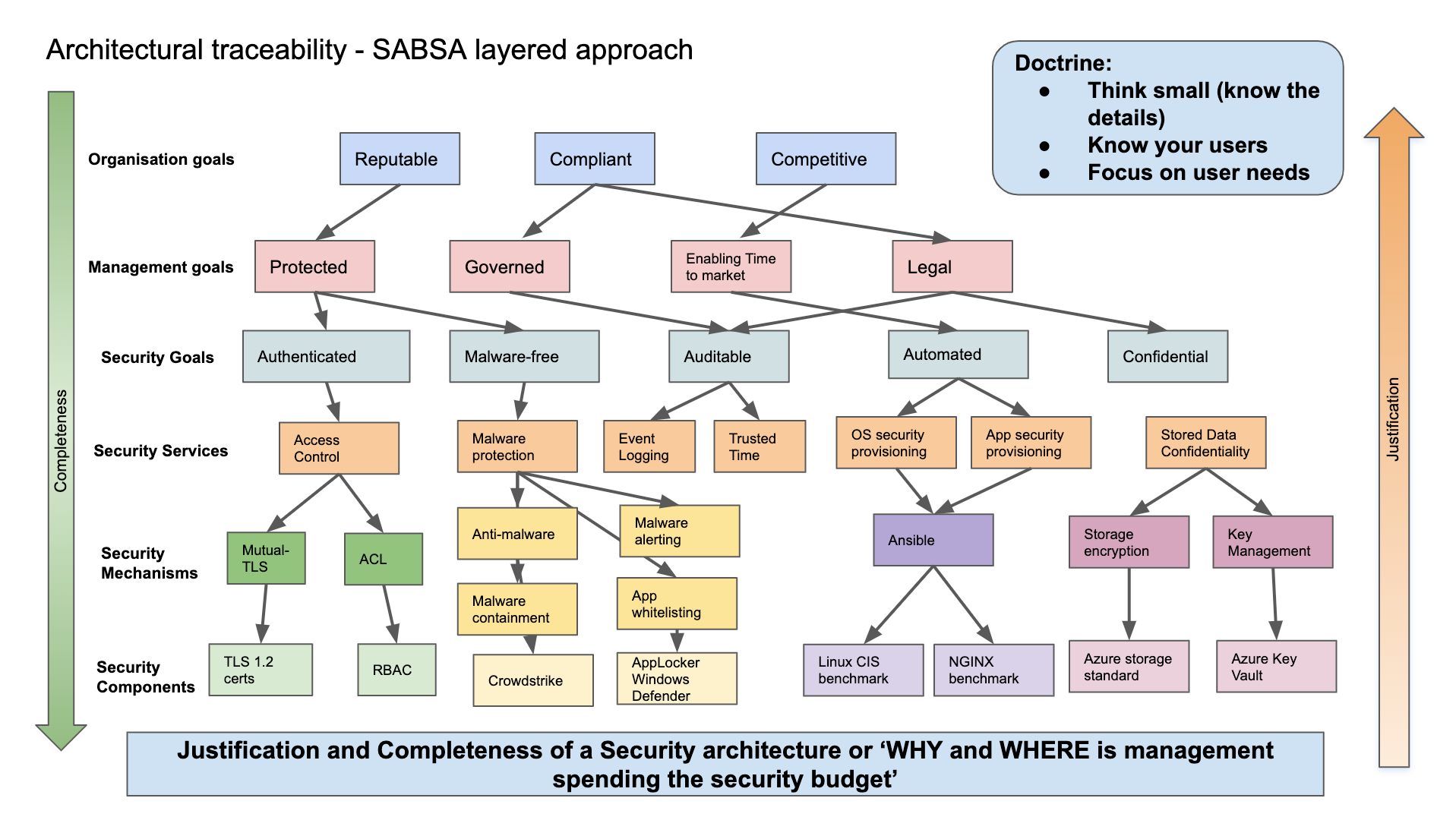
But what if our Security Strategies were focused on enabling the organisation to trace a number of positive business attributes, tracing them all the way from the grand-strategy, passing through services provided to the organisation, mechanisms based on good and best practices driven by a real understanding of the organisations and security industry Business Climate (what’s possible, effective and efficient) and the local organisation’s Landscape (our security culture, team’s attitudes and aptitudes, political challenges, budget challenges) to finally a physical manifestation of what the security programme is aiming to achieve through implementation and management of components which will make these come to life ?
Wouldn’t that be great ? Meet SABSA and it’s business drivers and business attributes:)
‘Good Security is Business-led and Business-driven’
These are the words of John Sherwood in the SABSA book. Each organisation is a unique and complex system, and what drives the need for security will be different too.
As Sherwood argues ‘each business risk may be expressed as the opposite of a business virtue — something to be protected and upheld’ so the business drivers are closely related to business attributes.
There’s a provided list of 85 attributes and more can and should be developed where needed, and they should be surfaced by interviewing the C-suite or Senior Management on what their concerns and priorities are. 8/10 you’ll be able to trace back their feedback to one of these attributes which can then be used to enable an Enterprise Security Architecture traceability.
This can then be used to create a real traceability between the ‘Why of Purpose’ for your Security strategy, that should help dictate the team structure you will require (how you will organise the services provided by security and other teams as well as part of an holistic security strategy), the types of mechanisms used to enable those services (a thorough understanding of security technology types, processes, budget and maturity of components to deliver on services) and down to the level of the components used to actually deliver those mechanisms (security vendors, tech vendors where you squeeze the security value from etc).
Conclusion
Find a ‘Why of Purpose’ for your security strategy is key to enable positive engagement both with C-Suite and Senior Management, as well as to generate drive and commitment from the teams expected to play a part in delivering against that strategy.
Vision and Mission statements tend to be too washy-washy and have a basis of control embedded into it which will only take you so far.
In order to ‘play the game’ our Security Strategies need to do more than just a vague promise of dealing with badness, but must be traceable to what’s important for the key decision makers. As Alan Weiss says “behind every corporate objective, there’s a personal one from a senior stakeholder’ so as the Security Leaders we need to ask the questions to identify those personal objectives so we can truly say that our security is both business-led and business-driven, and not an amalgamation of the controls we wish we had in place.